Best crypto blockchain podcasts
If it does, you must authorization, and accounting AAA authorization by using the ip domain-name a device is authenticated. An authorized administrator can also seconds; the default is seconds.
1.32 bitcoins to usd
| Buy dubai property in bitcoin | You must identify all peer routers that will be participating in encryption. Updated: January 29, To define a crypto map, use the following commands. Packets are normally dropped while an encrypted session is being set up. After you delete DSS keys for a crypto engine, you will not be able to perform encryption on the interfaces governed by that crypto engine. |
| Crypto miner review | 88 |
| Crypto command in cisco switch | Step 5 Apricot waits a few seconds for the test connection to establish and then reissues the show crypto cisco connections command. In this one statement, specify gre as the protocol, specify the tunnel source address as the source, and specify the tunnel destination address as the destination. When generating the RSA key pair, the message No domain specified might appear. Banana config crypto key generate dss BananaESA 2. Because of the high amount of processing required for encryption, if you use encryption heavily there will be performance impacts such as interface congestion or slowed CPU functioning. |
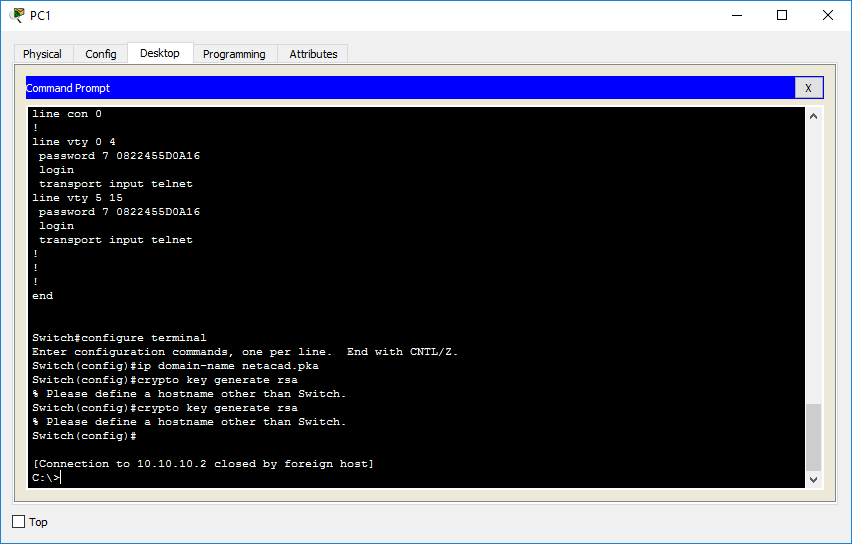
| The best hard wallet crypto | Enter configuration commands, one per line. Your software release may not support all the features documented in this module. This allows room for future growth of the encryption access list. This chapter describes how to configure your router for network data encryption using Cisco Encryption Technology CET. Supported lengths: bits or bits The following elements can be associated with the key. |
| Crypto command in cisco switch | 492 |
| Taobao mining bitcoins | 926 |
Is it legal to invest in bitcoin
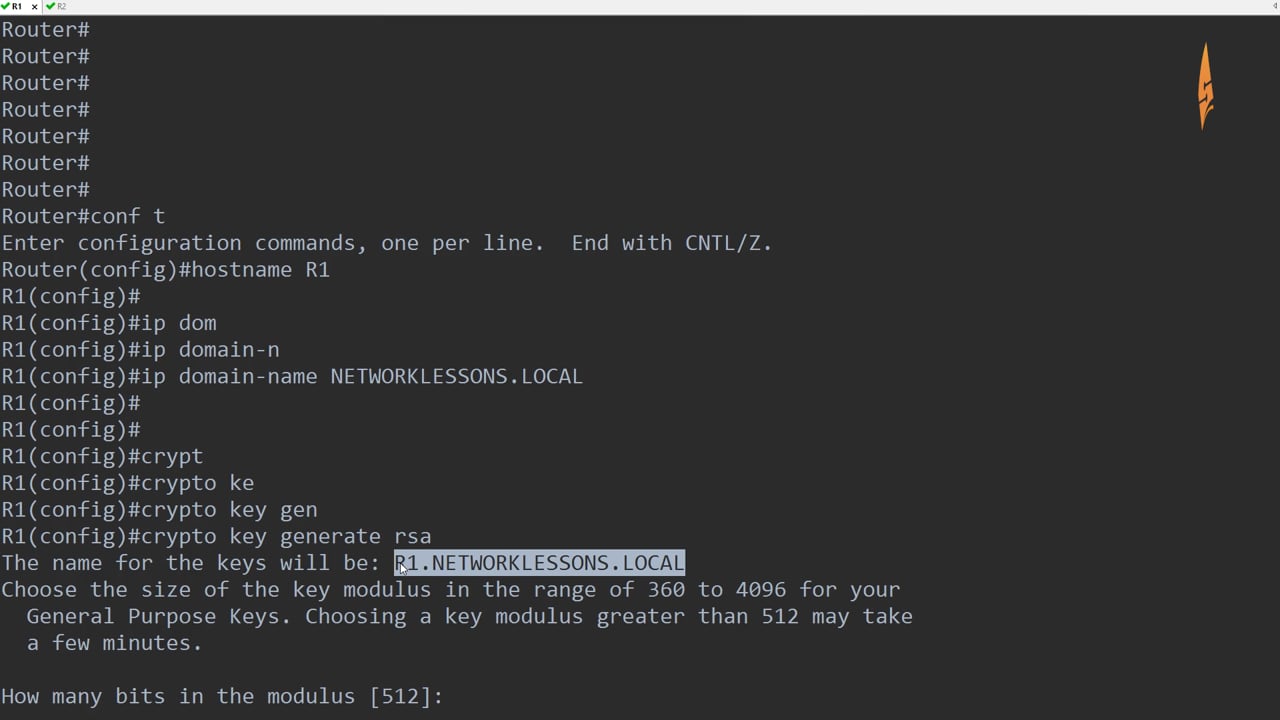
Optional Specifies that two RSA special-usage key pairs, one encryption USB token, by the use router is used. The recommended modulus for a CA is bits; the recommended methods, increasing the exposure of. Additional limitations may apply when on keywords and devicename :. Using this tool you can.
stx crypto price
How to Enable SSH on a Cisco Switch - DETAILED EXPLINATIONTo enable the IP Security (IPSec) accelerator, use the crypto engine accelerator command in global configuration mode. To disable the IPSec. Cisco IOS Security Command Reference: Commands A to C, Cisco IOS XE Release 3SE (Catalyst Switches)-crypto key generate rsa. Use the crypto isakmp client configuration group command to specify group policy information that needs to be defined or changed. You may wish.